Wargame/CTF
FwordCTF 2020 - Memory 2 (Forensics)
마띠(쥔장)
2020. 8. 31. 13:19

The analysis will be conducted on the given 'foren.raw' file in the previous step.
We already know OS information (imageinfo), so let's check the list of processes through 'pslist'.
.\volatility_2.6_win64_standalone.exe -f foren.raw --profile=Win7SP1x64 pslist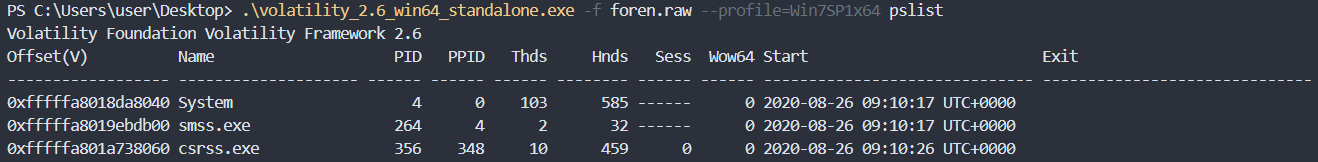
The problem texts "had a secret association" and "on Internet" give us a hint to analyze "chrome."
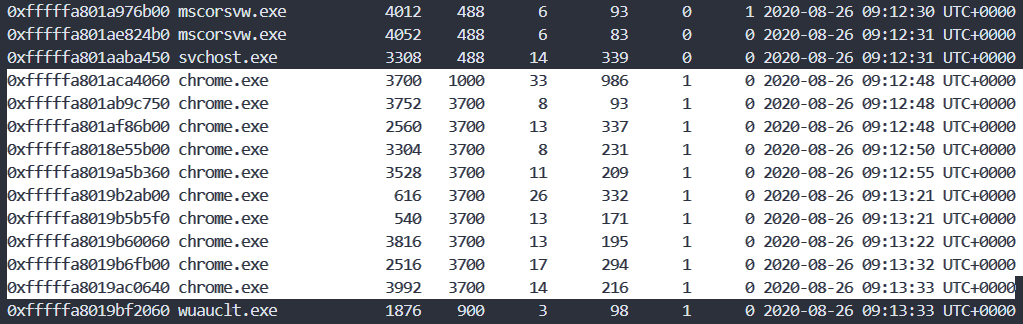
We will run 'yarascan' through the PID of the 'chrome.exe' in 'pslist', also we will search for strings that contain flag format together.
-Y option: string "FwordCTF{"
-p option: PID of 'chrom.exe'
.\volatility_2.6_win64_standalone.exe -f foren.raw --profile=Win7SP1x64 yarascan -Y "FwordCTF{" -p 3700,3752,2560,3304,3304,3528,616,540,3816,2516,3992Then you can see the flag.

flag: FwordCTF{top_secret_channel}
728x90